Table of contents
Open Table of contents
Einleitung
Für den perfekten Start mit VyOS und diversen Homelab Szenarien habe ich mir eine Grundkonfiguration erstellt, die den meisten eine gute Basis bietet und flexibel genug ist, um ausgebaut zu werden.
Ab der VyOS Version 1.4-rolling-202308040557 gab es eine Firewallsyntax Änderung, bei der sich die ganzen Befehle und Vorgehensweisen geändert haben. Nun gibt es nur noch die “zentrale” input, output und forwarding Chain an diese die eigenen Tables geknüpft werden. Mittels eines jump Befehls wird nun zur Table gesprungen. Vor der Umstellung gab es dediziert die input,forward Chain pro Interface, was eine bessere Übersicht geboten hat.
Das Konzept
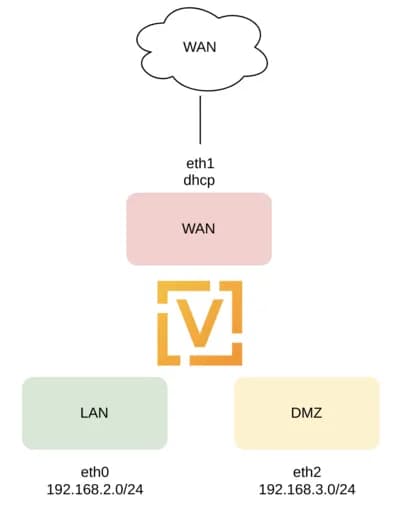
Die Konfiguration legt drei Netzwerke an: WAN, LAN und DMZ. WAN bezieht hierbei die Adresse via DHCP, LAN bekommt das Subnet 192.168.2.0/24 und DMZ das 192.168.3.0/24.
Besonderheiten:
- Keyboardlayout wird auf Deutsch gesetzt
- reboot-on-panic
- crtl-alt-delete für einen Neustart
- Nameserver des Systems wird auf 9.9.9.9 gesetzt
- Hostname “vyos”
- Systemhärtung unter der Rubrik Firewall
- Interface Gruppen (v4) WAN, LAN und DMZ werden auf die eth0,eth1,eth2 Interfaces gemapped
- Forward Chain ist default auf Drop
- input und output Chain ist default auf Accept
- dhcp Server im LAN Netzwerk
- Performance Anpassungen wenn benötigt
- SSH und ICMP auf WAN wird erlaubt
Nameskonzepte
Für die Benennung der Tables oder Interface kann natürlich jeder Namen hergenommen werden. In meiner Vorlage werden für die IPv4 und IPv6 Bezeichnungen ein v4- oder v6- vorgesetzt.
Interfaces: LAN, DMZ, WAN
Netzwerkgruppen: v4-rfc1918, v4-bogons
Firewall Table: v4-in-lan, v4-in-dmz, v4-in-wan
Die VyOS “configuration commands”
# System Config
set system config-management commit-revisions '100'
set system conntrack modules ftp
set system conntrack modules h323
set system conntrack modules nfs
set system conntrack modules pptp
set system conntrack modules sip
set system conntrack modules sqlnet
set system conntrack modules tftp
set system console device ttyS0 speed '115200'
set system host-name 'vyos'
set system syslog global facility all level 'info'
set system syslog global facility local7 level 'debug'
set system name-server '9.9.9.9'
set system option keyboard-layout de
set system option time-format '24-hour'
set system option ctrl-alt-delete 'reboot'
set system option reboot-on-panic
set system option startup-beep
# Interface Config
set interfaces ethernet eth0 address '192.168.2.1/24'
set interfaces ethernet eth0 description 'LAN'
set interfaces ethernet eth1 address 'dhcp'
set interfaces ethernet eth1 description 'WAN'
set interfaces ethernet eth2 address '192.168.3.1/24'
set interfaces ethernet eth2 description 'DMZ'
set interfaces loopback lo
# Firewall Config
set firewall global-options all-ping 'enable'
set firewall global-options broadcast-ping 'disable'
set firewall global-options ip-src-route 'disable'
set firewall global-options ipv6-receive-redirects 'disable'
set firewall global-options ipv6-src-route 'disable'
set firewall global-options log-martians 'enable'
set firewall global-options receive-redirects 'disable'
set firewall global-options resolver-cache
set firewall global-options resolver-interval '60'
set firewall global-options send-redirects 'disable'
set firewall global-options source-validation 'strict'
set firewall global-options syn-cookies 'enable'
set firewall global-options twa-hazards-protection 'disable'
set firewall group interface-group DMZ interface 'eth2'
set firewall group interface-group LAN interface 'eth0'
set firewall group interface-group WAN interface 'eth1'
set firewall group ipv6-network-group v6-dmz
set firewall group ipv6-network-group v6-lan
set firewall group ipv6-network-group v6-wan network '::/0'
set firewall group network-group v4-bogons network '0.0.0.0/8'
set firewall group network-group v4-bogons network '10.0.0.0/8'
set firewall group network-group v4-bogons network '100.64.0.0/10'
set firewall group network-group v4-bogons network '127.0.0.0/8'
set firewall group network-group v4-bogons network '169.254.0.0/16'
set firewall group network-group v4-bogons network '172.16.0.0/12'
set firewall group network-group v4-bogons network '192.0.0.0/24'
set firewall group network-group v4-bogons network '192.0.2.0/24'
set firewall group network-group v4-bogons network '192.168.0.0/16'
set firewall group network-group v4-bogons network '198.18.0.0/15'
set firewall group network-group v4-bogons network '198.51.100.0/24'
set firewall group network-group v4-bogons network '203.0.113.0/24'
set firewall group network-group v4-bogons network '224.0.0.0/4'
set firewall group network-group v4-bogons network '240.0.0.0/4'
set firewall group network-group v4-dmz network '192.168.3.0/24'
set firewall group network-group v4-lan network '192.168.2.0/24'
set firewall group network-group v4-rfc1918 network '10.0.0.0/8'
set firewall group network-group v4-rfc1918 network '172.16.0.0/12'
set firewall group network-group v4-rfc1918 network '192.168.0.0/16'
set firewall ipv4 forward filter default-action 'drop'
set firewall ipv4 forward filter rule 10 action 'accept'
set firewall ipv4 forward filter rule 10 state established 'enable'
set firewall ipv4 forward filter rule 20 action 'accept'
set firewall ipv4 forward filter rule 20 state related 'enable'
set firewall ipv4 forward filter rule 30 action 'drop'
set firewall ipv4 forward filter rule 30 state invalid 'enable'
set firewall ipv4 forward filter rule 40 action 'jump'
set firewall ipv4 forward filter rule 40 jump-target 'v4-in-wan'
set firewall ipv4 forward filter rule 40 inbound-interface interface-group 'WAN'
set firewall ipv4 forward filter rule 50 action 'jump'
set firewall ipv4 forward filter rule 50 jump-target 'v4-in-dmz'
set firewall ipv4 forward filter rule 50 inbound-interface interface-group 'DMZ'
set firewall ipv4 forward filter rule 60 action 'jump'
set firewall ipv4 forward filter rule 60 jump-target 'v4-in-lan'
set firewall ipv4 forward filter rule 60 inbound-interface interface-group 'LAN'
set firewall ipv4 input filter default-action 'accept'
set firewall ipv4 input filter rule 10 action 'accept'
set firewall ipv4 input filter rule 10 state established 'enable'
set firewall ipv4 input filter rule 20 action 'accept'
set firewall ipv4 input filter rule 20 state related 'enable'
set firewall ipv4 input filter rule 30 action 'drop'
set firewall ipv4 input filter rule 30 state invalid 'enable'
set firewall ipv4 input filter rule 999999 action 'accept'
set firewall ipv4 input filter rule 999999 inbound-interface interface-name 'lo'
set firewall ipv4 input filter rule 999999 source address '127.0.0.0/8'
set firewall ipv4 name v4-in-dmz default-action 'drop'
set firewall ipv4 name v4-in-lan default-action 'drop'
set firewall ipv4 name v4-in-wan default-action 'drop'
set firewall ipv4 output filter default-action 'accept'
set firewall ipv4 output filter rule 10 action 'accept'
set firewall ipv4 output filter rule 10 state established 'enable'
set firewall ipv4 output filter rule 20 action 'accept'
set firewall ipv4 output filter rule 20 state related 'enable'
set firewall ipv4 output filter rule 30 action 'drop'
set firewall ipv4 output filter rule 30 state invalid 'enable'
set firewall ipv4 output filter rule 999999 action 'accept'
set firewall ipv4 output filter rule 999999 destination address '127.0.0.0/8'
set firewall ipv4 output filter rule 999999 outbound-interface interface-name 'lo'
set firewall ipv6 forward filter default-action 'drop'
set firewall ipv6 forward filter rule 10 action 'accept'
set firewall ipv6 forward filter rule 10 state established 'enable'
set firewall ipv6 forward filter rule 20 action 'accept'
set firewall ipv6 forward filter rule 20 state related 'enable'
set firewall ipv6 forward filter rule 30 action 'drop'
set firewall ipv6 forward filter rule 30 state invalid 'enable'
set firewall ipv6 forward filter rule 40 action 'jump'
set firewall ipv6 forward filter rule 40 jump-target 'v6-in-wan'
set firewall ipv6 forward filter rule 40 inbound-interface interface-group 'WAN'
set firewall ipv6 forward filter rule 50 action 'jump'
set firewall ipv6 forward filter rule 50 jump-target 'v6-in-dmz'
set firewall ipv6 forward filter rule 50 inbound-interface interface-group 'DMZ'
set firewall ipv6 forward filter rule 60 action 'jump'
set firewall ipv6 forward filter rule 60 jump-target 'v6-in-lan'
set firewall ipv6 forward filter rule 60 inbound-interface interface-group 'LAN'
set firewall ipv6 input filter default-action 'accept'
set firewall ipv6 input filter rule 10 action 'accept'
set firewall ipv6 input filter rule 10 state established 'enable'
set firewall ipv6 input filter rule 20 action 'accept'
set firewall ipv6 input filter rule 20 state related 'enable'
set firewall ipv6 input filter rule 30 action 'drop'
set firewall ipv6 input filter rule 30 state invalid 'enable'
set firewall ipv6 input filter rule 999999 action 'accept'
set firewall ipv6 input filter rule 999999 inbound-interface interface-name 'lo'
set firewall ipv6 input filter rule 999999 source address '::1/128'
set firewall ipv6 name v6-in-dmz default-action 'drop'
set firewall ipv6 name v6-in-lan default-action 'drop'
set firewall ipv6 name v6-in-wan default-action 'drop'
set firewall ipv6 output filter default-action 'accept'
set firewall ipv6 output filter rule 10 action 'accept'
set firewall ipv6 output filter rule 10 state established 'enable'
set firewall ipv6 output filter rule 20 action 'accept'
set firewall ipv6 output filter rule 20 state related 'enable'
set firewall ipv6 output filter rule 30 action 'drop'
set firewall ipv6 output filter rule 30 state invalid 'enable'
set firewall ipv6 output filter rule 999999 action 'accept'
set firewall ipv6 output filter rule 999999 destination address '::1/128'
set firewall ipv6 output filter rule 999999 outbound-interface interface-name 'lo'
# WAN Firewall rules
set firewall ipv4 name v4-in-wan rule 100 action 'accept'
set firewall ipv4 name v4-in-wan rule 100 destination port '22'
set firewall ipv4 name v4-in-wan rule 100 description 'Allow SSH on WAN'
set firewall ipv4 name v4-in-wan rule 100 protocol 'tcp'
set firewall ipv4 name v4-in-wan rule 100 state new 'enable'
set firewall ipv4 name v4-in-wan rule 130 action accept
set firewall ipv4 name v4-in-wan rule 130 description "Allow ICMP"
set firewall ipv4 name v4-in-wan rule 130 source group network-group v4-lan
set firewall ipv4 name v4-in-wan rule 130 protocol icmp
# LAN Firewall rules
set firewall ipv4 name v4-in-lan rule 100 action accept
set firewall ipv4 name v4-in-lan rule 100 description "Allow Web Traffic"
set firewall ipv4 name v4-in-lan rule 100 source group network-group v4-lan
set firewall ipv4 name v4-in-lan rule 100 destination port 80,443
set firewall ipv4 name v4-in-lan rule 100 protocol tcp_udp
set firewall ipv4 name v4-in-lan rule 130 action accept
set firewall ipv4 name v4-in-lan rule 130 description "Allow ICMP"
set firewall ipv4 name v4-in-lan rule 130 source group network-group v4-lan
set firewall ipv4 name v4-in-lan rule 130 protocol icmp
set firewall ipv4 name v4-in-lan rule 160 action accept
set firewall ipv4 name v4-in-lan rule 160 description "Allow SSH OUT"
set firewall ipv4 name v4-in-lan rule 160 destination port 22
set firewall ipv4 name v4-in-lan rule 160 source group network-group v4-lan
set firewall ipv4 name v4-in-lan rule 160 protocol tcp
# DMZ Firewall rules
set firewall ipv4 name v4-in-dmz rule 100 action drop
set firewall ipv4 name v4-in-dmz rule 100 description "Block all RFC1918 Traffic"
set firewall ipv4 name v4-in-dmz rule 100 source group network-group v4-dmz
set firewall ipv4 name v4-in-dmz rule 100 destination group network-group v4-rfc1918
set firewall ipv4 name v4-in-dmz rule 100 protocol all
set firewall ipv4 name v4-in-dmz rule 130 action accept
set firewall ipv4 name v4-in-dmz rule 130 description "Allow Web Traffic"
set firewall ipv4 name v4-in-dmz rule 130 source group network-group v4-dmz
set firewall ipv4 name v4-in-dmz rule 130 destination port 80,443
set firewall ipv4 name v4-in-dmz rule 130 protocol tcp_udp
# NAT Config
set nat source rule 100 outbound-interface 'eth1'
set nat source rule 100 source address '192.168.2.0/24'
set nat source rule 100 translation address 'masquerade'
set nat source rule 101 outbound-interface 'eth1'
set nat source rule 101 source address '192.168.3.0/24'
set nat source rule 101 translation address 'masquerade'
# Services Config
set service dhcp-server shared-network-name LAN authoritative
set service dhcp-server listen-address '192.168.2.1'
set service dhcp-server shared-network-name LAN name-server '192.168.2.1'
set service dhcp-server shared-network-name LAN subnet 192.168.2.0/24 default-router '192.168.2.1'
set service dhcp-server shared-network-name LAN subnet 192.168.2.0/24 range range0 start '192.168.2.100'
set service dhcp-server shared-network-name LAN subnet 192.168.2.0/24 range range0 stop '192.168.2.200'
set service dns forwarding allow-from '192.168.3.0/24'
set service dns forwarding allow-from '192.168.2.0/24'
set service dns forwarding cache-size '0'
set service dns forwarding listen-address '192.168.2.1'
set service dns forwarding listen-address '192.168.3.1'
set service dns forwarding name-server 9.9.9.9
set service ntp allow-client address '0.0.0.0/0'
set service ntp allow-client address '::/0'
set service ntp server time1.vyos.net
set service ntp server time2.vyos.net
set service ntp server time3.vyos.net
set service ssh port '22'
# Performace Config
set interfaces ethernet ethX offload gro
set interfaces ethernet ethX offload gso
set interfaces ethernet ethX offload lro
set interfaces ethernet ethX offload rfs
set interfaces ethernet ethX offload rps
set interfaces ethernet ethX offload sg
set interfaces ethernet ethX offload tso
set interfaces ethernet ethX ring-buffer rx '4096'
set interfaces ethernet ethX ring-buffer tx '4096'
set system option performance 'throughput'
set system conntrack expect-table-size '10485760'
set system conntrack hash-size '10485760'
set system conntrack log icmp new
set system conntrack log other new
set system conntrack log tcp new
set system conntrack log udp new
set system conntrack table-size '10485760'
set system conntrack timeout icmp '10'
set system conntrack timeout other '600'
set system conntrack timeout tcp close '10'
set system conntrack timeout tcp close-wait '30'
set system conntrack timeout tcp established '600'
set system conntrack timeout tcp fin-wait '30'
set system conntrack timeout tcp last-ack '30'
set system conntrack timeout tcp syn-recv '30'
set system conntrack timeout tcp syn-sent '30'
set system conntrack timeout tcp time-wait '30'
set system conntrack timeout udp other '600'
set system conntrack timeout udp stream '600'
set system ip arp table-size '32768'
set system ip disable-directed-broadcast
set system ip multipath layer4-hashing
# Enable below to disable IPv6 forwarding:
#set system ipv6 disable-forwarding
set system ipv6 multipath layer4-hashing
set system ipv6 neighbor table-size '32768'
#Test only - Congestion control
set system sysctl parameter net.core.default_qdisc value 'fq_codel'
set system sysctl parameter net.ipv4.tcp_congestion_control value 'bbr'
## along with adding this to /config/scripts/vyos-preconfig-bootup.script
/sbin/modprobe tcp_bbrKonfiguration erweitern
Weiteres Netzwerk hinzufügen:
- Ethernet Interface konfigurieren
set interfaces ethernet eth3 address '192.168.0.1/24'
set interfaces ethernet eth3 description 'DMZ-Server'- Netzwerk Gruppe
v4-dmz-serveranlegen
set firewall group network-group v4-dmz-server network '192.168.0.1/24'- Interface Gruppe anlegen
set firewall group interface-group dmz-server interface 'eth3'- Firewall Table in forward verknüpfen
set firewall ipv4 forward filter rule 70 action 'jump'
set firewall ipv4 forward filter rule 70 jump-target 'v4-in-dmz-server'
set firewall ipv4 forward filter rule 70 inbound-interface interface-group 'DMZ-Server'- Ein default Drop in der Chain “v4-in-dmz-server”
set firewall ipv4 name v4-in-dmz-server default-action 'drop'- Http, Https Traffic erlauben
set firewall ipv4 name v4-in-dmz-server rule 100 action accept
set firewall ipv4 name v4-in-dmz-server rule 100 description "Allow Web Traffic"
set firewall ipv4 name v4-in-dmz-server rule 100 source group network-group v4-dmz-server
set firewall ipv4 name v4-in-dmz-server rule 100 destination port 80,443
set firewall ipv4 name v4-in-dmz-server rule 100 protocol tcp_udpFirewallregeln erweitern
Neue Port Gruppen für z.B. Mailing anlegen
set firewall group port-group mailing_ports port 993
set firewall group port-group mailing_ports port 465Firewallregeln in der LAN Table hinzufügen. Hier wird die v4-lan-Gruppe erlaubt, aus den Netzwerk 192.168.2.0/24 heraus, Port 993 und 465 zu verwenden. Somit könnt ihr nun E-Mails senden.
set firewall ipv4 name v4-in-lan rule 180 action accept
set firewall ipv4 name v4-in-lan rule 180 description "Allow Mailing"
set firewall ipv4 name v4-in-lan rule 180 destination group port-group 'mailing_ports'
set firewall ipv4 name v4-in-lan rule 180 source group network-group v4-lan
set firewall ipv4 name v4-in-lan rule 180 protocol tcp